- On Aug 18, 2022 10:06:38 PM
- by: Joe Rudolph
- 5 minutes Read
Did you know that your employees are your biggest cybersecurity risk?
It’s true – 71% of cybersecurity breaches started with a phishing email and a well-meaning employee with a gap in technical knowledge. This means that every employee in your organization needs recurring training in the technology that they use in their day-to-day life.
If you think your small business is ready for any cyber attack, remember that Cybersecurity Ventures Magazine expects global cybercrime costs to reach $10.5 trillion each year by 2025. What can cover your security gaps (i.e., employees who are not tech-savvy) to prepare for these inevitable attacks?
One of the first steps towards a proactive cybersecurity risk plan is to help everyone in your company understand basic cybersecurity terms. This blog post focuses on helping you do just that, by defining the most common cybersecurity terminology that everyone in your organization should be familiar with.
1. Cybersecurity
Of course, before defining other terms, it’s crucial to understand what cybersecurity means. According to IBM:
Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Also known as information technology (IT) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization.
As mentioned earlier, many – but not all – cybersecurity threats stem from your own employees. That’s why cybersecurity training is so important.
2. Domains
The next basic cybersecurity term is domains. HubSpot defines a domain as follows:
“A domain is a part of the web address nomenclature someone would use to find your website or a page of your website online. It is a string of text associated with the numerical IP address of a website.”
Domain security is important to protect both company data accessible through networked computers and supplied user data who access a domain. One of the most significant phishing scams is perpetrated using domain hijacking where users are redirected to another website for the purpose of harvesting their personal data.
3. Exploit
In cybersecurity, an exploit is a specific type of script or code that is malicious. An exploit is meant to use a computer’s vulnerability to breach a network. This type of cyberattack opens the door for malware to be installed on a device.
4. Malware
You’ve probably heard the term malware before. It’s more of a categorical term than a singular threat. Malware refers to any type of malicious software – including viruses, worms, Trojan viruses, spyware, adware, and ransomware. Malware is the vehicle that is used to harvest a small business’ data during a breach.
5. Cloud
The cloud feels like a buzzword these days as everyone is seemingly obsessed with cloud-enablement. For many, the definition of ‘the cloud’ is still a bit unclear. When referring to technology, the cloud is another way of saying “hosted in an internet accessible datacenter.”
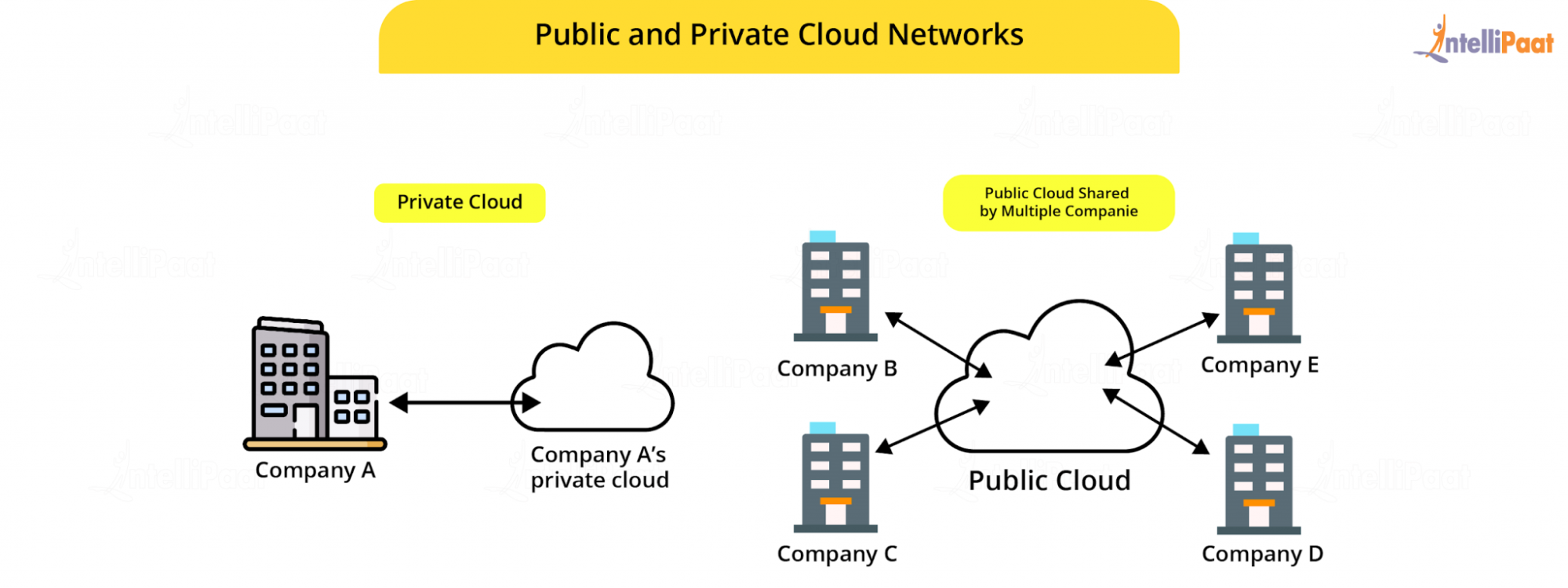
More specifically, it refers to a global network of computers and servers that can store and access data from anywhere, anytime. In the early days of the internet, most company data was stored on computer hard drives and companies maintained server networks in-house. Now, even small businesses can easily utilize cloud-based systems.
With the cloud, data is stored on remote servers dispersed around the world, connected by the internet. Cloud storage provides greater accessibility across users and devices.
6. VPN
A virtual private network, or VPN, has become a cybersecurity staple as companies have increasingly adopted remote and mobile working arrangements. A VPN uses authentication to provide secure access to a company network using a public network access point.
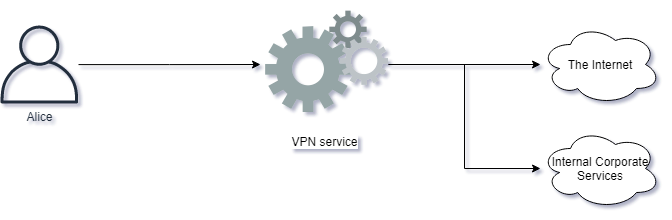
A VPN serves to ensure that intended online activity remains private, safe from prying eyes that may otherwise be able to gain access to sensitive company data.
7. Multi-Factor Authentication (MFA)
Multi-Factor authentication, or MFA, is an underutilized but powerful tool for protecting cybersecurity. It goes beyond password protection and requires users to use two or more forms of authentication to gain access to a device, network, or content.
Passwords are something your employees know, but they are a vulnerability since a hacker could guess them, or your employees could unknowingly give away their password (through malware, phishing, etc.).
"If whatever service your employees are using offers MFA, enable it as soon as possible. It stops hacking dead in its tracks.”
Joe Rudolph, Privacy and Security Officer at Ceeva
MFA uses a combination of verifiable data points like passwords, device access, and biometrics to add extra layers of security to access points. For example, users may be required to input a password and then receive and input a code on a separate device in their possession. This acts as multiple barriers that make it almost impossible for someone to breach.
Some employees are required to change their passwords regularly, or at least cover Two-Factor Authentication (2FA) in their regular cybersecurity training programs. Having a minimum requirement of 2FA for your employees’ devices can greatly increase your company’s security.
8. Breach
When the conversation turns to cybersecurity, there are certain words that always seem to come up. The first, and scariest, is a cybersecurity breach. A breach happens when an unauthorized party has gained access to a secure network. One concerning realization is that breaches can occur undetected.
In fact, IBM released a report that indicates the average time to detect and contain a breach is 287 days. This means that it might not always be obvious when a breach has occurred. Often, a breach is tied to a timed event and the unauthorized party is waiting to exploit, or take advantage of, a specific event.
If you’re getting unsure if training is right for your employees, discover the benefits of end user cybersecurity awareness training.
9. Vulnerability
A vulnerability, on the other hand, is a weak spot or an opportunity for a breach. Exposing a vulnerability doesn’t mean that a network has been hacked, it means there is a possibility that a breach could occur. The best line of defense in cybersecurity begins with assessing security measures and identifying vulnerabilities.
If companies actively assess their cybersecurity measures and address vulnerabilities, they can proactively stop a breach before it happens.
Knowing Basic Cybersecurity Terms Can Save Your Business
Building awareness to support a strong cybersecurity program across your organization begins with common language. Providing basic technology skills training to all employees who access devices on your company network is a prerequisite for managing any cybersecurity risks for small businesses.
Armed with this new knowledge of basic cybersecurity terms, your organization will be in a better position to understand threats and minimize vulnerabilities. However, it’s not an easy job, and many businesses turn to experts for help.
Ceeva’s MSP IT experts can help you fill in the gaps with our full selection of tailored cybersecurity to meet all your needs. Set up a training and testing program with Ceeva’s cybersecurity experts today, and protect your business from risks!
Subscribe blog for latest updates
By submitting this you will be receiving our latest updates on post.
